👷♂️Detection Handling
Scanning
The Malware Detection scan starts automatically, without any need for initialization. It is being run asynchronously in a separate thread along with other freeRASP checks, so it has no significant impact either on the application or freeRASP checks performance.
Based on the provided blacklists, Malware Detection examines installed applications to determine if they match any configurations listed in the blacklist.
Scanning may take longer when using a hash-based blacklist, as the apk hash must be computed for each app on the device, which can be an expensive operation. More about hash-based blacklist here.
System Applications
To avoid false positives, system applications are filtered out from:
Permission-based blacklist
Installation sources whitelist
and therefore won't be present in the results of scan.
Processing Scan Results
Receiving Results
The results of the scan are received using a callback mechanism from the freeRASP SDK by triggering malware callback:
// The following callback from the ThreatListener.ThreatDetected has to be implemented:
override fun onMalwareDetected(p0: MutableList<SuspiciousAppInfo>?) {
TODO("Not yet implemented")
}// The following callback from the ThreatCallback has to be provided:
final callback = ThreatCallback(
onMalware: (susApps) {
// TODO: Not yet implemented
}
// Other callbacks...
);// The following callback in the actions object has to be provided:
import { type SuspiciousAppInfo } from 'freerasp-react-native';
const actions = {
...
// Android only
malware: (suspiciousApps: SuspiciousAppInfo[]) => {
console.log('Detected suspicious apps: ', suspiciousApps);
},
},Learn more about the callbacks here; see the respective platform.
Result Interpretation
After the scan is complete, freeRASP provides a result - a list of suspicious applications.
Each suspicious application in the list includes two main components:
SuspiciousAppInfo An object containing details about the application.
Reason A string explaining why the application was flagged as suspicious.
SuspiciousAppInfo object contains two properties:
packageInfoInformation about the contents of a package of the application, such as package name, version, and other relevant details.
Refers to the entire PackageInfo object.
reasonContains String value with the information about which blacklist has been matched (for information about blacklists, see Features). Possible values are:
blacklist- if at least one of the following conditions holds for the application:a package name has been matched with a package name in a packageNames blacklist, or
an application hash has been matched with an application hash in the hashes blacklist.
suspiciousPermission- if both of the following conditions hold for the application:the application contains at least one of the suspicious groups of permissions, and
the application is installed from a non-whitelisted source.
installSource- if the application is installed from a non-whitelisted source.
If suspiciousPermission conditions hold as well, these take priority over the installSource for the
reasonvalue.
SuspiciousAppInfo object is composed of two variables:
packageInfoPackageInfo - information about the contents of a package of the application, e.g., package name, version, and other relevant details.
packageInfoconsists of:packageName- type String - the name of the package. From the tag'snameattribute.appName- type String? - public name of the package, or undefined if not available. From theandroid:nameattribute.version- type String? - the version name of the package as specified by the tag'sversionNameattribute, or undefined if not available.installerStore- type String? - the name of the package responsible for the installation, or undefined if not available.appIcon- type String? - the icon associated with an application. Returns PNG encoded as a base64 string, or undefined if icon is not available. The icon can then be displayed:using
Imagewidget:
reasontype String - the information about which blacklist has been matched (for information about blacklists, see Features).
blacklist - if at least one of the following conditions holds for the application:
a package name has been matched with a package name in a packageNames blacklist,
an application hash has been matched with an application hash in the hashes blacklist.
suspiciousPermission - if both of the following conditions hold for the application:
the application contains at least one of the suspicious groups of permissions,
the application is installed from a not-whitelisted source.
installSource - if the application is installed from a not-whitelisted source.
If suspiciousPermission conditions hold as well, these take priority over the installSource for the reason value.
SuspiciousAppInfo object is composed of two variables:
packageInfoPackageInfo - information about the contents of a package of the application, e.g., package name, version, and other relevant details.
packageInfoconsists of:packageName- type string - the name of the package. From the tag'snameattribute.appName- type string? - public name of the package, or undefined if not available. From theandroid:nameattribute.version- type string? - the version name of the package as specified by the tag'sversionNameattribute, or undefined if not available.installerStore- type string? - the name of the package responsible for the installation, or undefined if not available.appIcon- type string? - the icon associated with an application. Returns PNG encoded as a base64 string, or undefined if icon is not available. The icon can then be displayed:using the standard
Imagecomponent:
reasontype string - the information about which blacklist has been matched (for information about blacklists, see Features).
blacklist - if at least one of the following conditions holds for the application:
a package name has been matched with a package name in a packageNames blacklist,
an application hash has been matched with an application hash in the hashes blacklist.
suspiciousPermission - if both of the following conditions hold for the application:
the application contains at least one of the suspicious groups of permissions,
the application is installed from a not-whitelisted source.
installSource - if the application is installed from a not-whitelisted source.
If suspiciousPermission conditions hold as well, these take priority over the installSource for the reason value.
SuspiciousAppInfo object is composed of two variables:
packageInfoPackageInfo - information about the contents of a package of the application, e.g., package name, version, and other relevant details.
packageInfoconsists of:packageName- type string - the name of the package. From the tag'snameattribute.appName- type string? - public name of the package, or undefined if not available. From theandroid:nameattribute.version- type string? - the version name of the package as specified by the tag'sversionNameattribute, or undefined if not available.installerStore- type string? - the name of the package responsible for the installation, or undefined if not available.appIcon- type string? - the icon associated with an application. Returns PNG encoded as a base64 string, or undefined if icon is not available. The icon can then be displayed:using the standard
imgcomponent:
reasontype string - the information about which blacklist has been matched (for information about blacklists, see Features).
blacklist - if at least one of the following conditions holds for the application:
a package name has been matched with a package name in a packageNames blacklist,
an application hash has been matched with an application hash in the hashes blacklist.
suspiciousPermission - if both of the following conditions hold for the application:
the application contains at least one of the suspicious groups of permissions,
the application is installed from a not-whitelisted source.
installSource - if the application is installed from a not-whitelisted source.
If suspiciousPermission conditions hold as well, these take priority over the installSource for the reason value.
SuspiciousAppInfo object is composed of two variables:
packageInfoPackageInfo - information about the contents of a package of the application, e.g., package name, version, and other relevant details.
packageInfoconsists of:packageName- type string - the name of the package. From the tag'snameattribute.appName- type string? - public name of the package, or undefined if not available. From theandroid:nameattribute.version- type string? - the version name of the package as specified by the tag'sversionNameattribute, or undefined if not available.installerStore- type string? - the name of the package responsible for the installation, or undefined if not available.appIcon- type string? - the icon associated with an application. Returns PNG encoded as a base64 string, or undefined if icon is not available. The icon can then be displayed:using the standard
ion-imgcomponent:
reasontype string - the information about which blacklist has been matched (for information about blacklists, see Features).
blacklist - if at least one of the following conditions holds for the application:
a package name has been matched with a package name in a packageNames blacklist,
an application hash has been matched with an application hash in the hashes blacklist.
suspiciousPermission - if both of the following conditions hold for the application:
the application contains at least one of the suspicious groups of permissions,
the application is installed from a not-whitelisted source.
installSource - if the application is installed from a not-whitelisted source.
If suspiciousPermission conditions hold as well, these take priority over the installSource for the reason value.
Caching
Scanned applications are stored in a cache until all applications on the device have been scanned. Only after the entire scan is complete , the callback mechanism sends the results to the application.
For example, if the application is only open for a few seconds and only a portion of the scan is completed, the results will be available the next time the application is opened for a longer period.
If any changes are made to the configuration—such as modifying a blacklist in the TalsecConfig—the cache is cleared, and the scanning process restarts from the beginning. This ensures that all applications are re-scanned under the latest security settings.
Result Handling
The results can be handled in many different ways.
For example:
Logging on the back-end Collect data about found suspicious applications and potential threats (or even whitelists in case of "false positives"). However, be aware that Google considers package names as personal and sensitive information, so special requirements apply to their collection.
Blocking certain logic if a specific application (or type of application) is detected.
Showcase the results Suggest to the user that they can add the application to the whitelist or navigate them to uninstall the application.
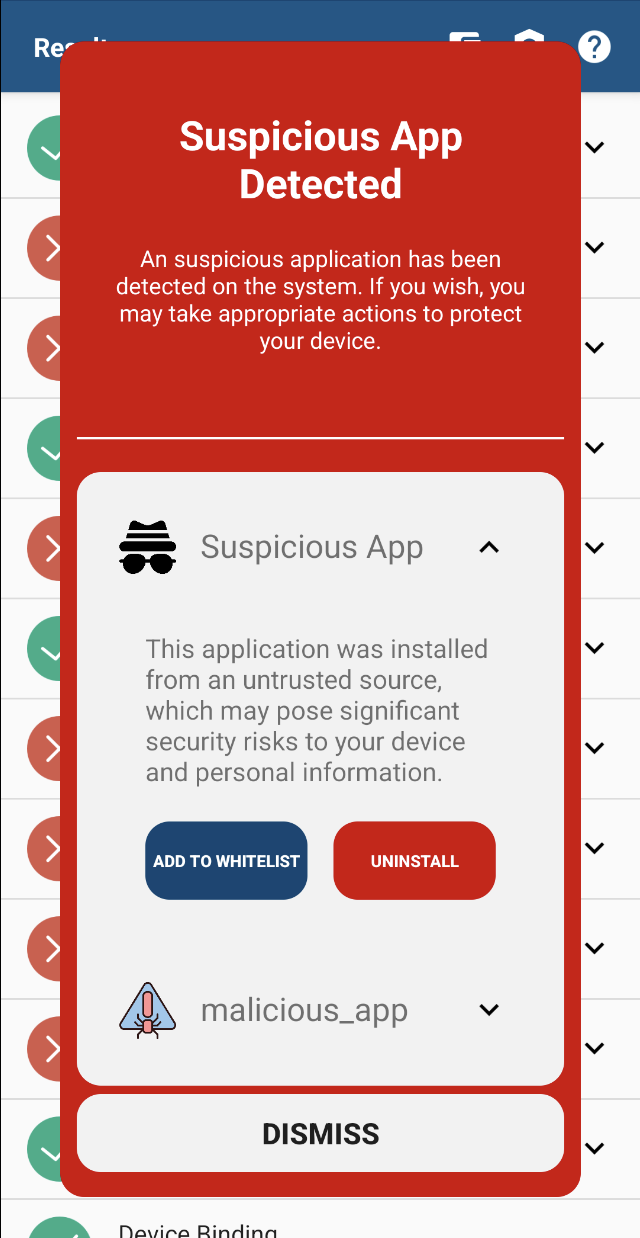
Tip
On Android (i.e. not hybrid platforms), if you want to uninstall the application (noted below as item), you can use the following code snippet to navigate directly to the system settings where the application can be uninstalled:
Last updated

