🚀A Developer’s Guide to Implement End-to-End Encryption in Mobile Apps 🛡️

Introduction
In today’s digital age, mobile apps have become the backbone of modern communication, financial transactions, and personal data storage. However, with this convenience comes an ever-present threat: eavesdropping. Malicious actors are constantly on the lookout for vulnerabilities in communication channels, exploiting them to intercept sensitive data such as passwords, messages, and payment details.
This is where End-to-End Encryption (E2EE) steps in as a guardian of privacy. By ensuring that data is encrypted from the moment it leaves the sender’s device until it is decrypted on the receiver’s device, E2EE renders intercepted data unreadable, providing robust protection against eavesdropping attacks.
In this article, we’ll explore:
▶️What eavesdropping is and its impact on mobile app security.
▶️The principles and benefits of E2EE.
▶️When to use E2EE.
▶️Step-by-step guidance on implementing E2EE in mobile apps, with practical examples for Flutter developers.
Whether you’re building a messaging app, a financial platform, or any app handling sensitive user data, mastering end-to-end encryption is a critical skill for modern developers. Let’s dive in and learn how to fortify your apps against eavesdropping and safeguard user trust.

Ahmed Ayman: I’m a passionate Mobile Engineer with over 7 years of experience in building high-performance applications. I love sharing knowledge, mentoring developers, and writing technical articles to contribute to the tech community. My focus is on scalability, performance optimization, and crafting seamless user experiences through efficient and maintainable solutions. Ahmed Ayman | LinkedIn | Senior Flutter Mobile Developer
What Eavesdropping Is and Its Impact on Mobile App Security?
Eavesdropping is a cyberattack where an unauthorized party intercepts and listens to or views private communications between two entities. For mobile apps, this often involves malicious actors exploiting vulnerabilities in network communication to access sensitive user data.
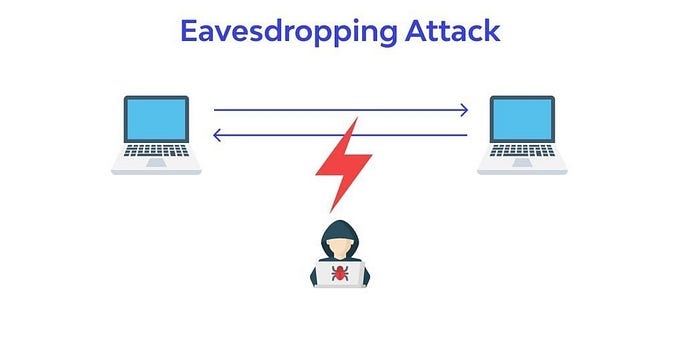
How Eavesdropping Happens
Eavesdropping can occur through various attack vectors, such as:
Network Sniffing: Attackers use tools to capture unencrypted data sent over public Wi-Fi or unsecured networks.
Man-in-the-Middle (MITM) Attacks: Malicious actors position themselves between the sender and receiver, intercepting and possibly modifying the data.
Malicious Software: Spyware or other malware installed on the device can monitor communications.
Outdated Protocols: Using outdated encryption standards (e.g., TLS 1.0) leaves communications vulnerable.
The Impact on Mobile App Security
Eavesdropping attacks can have severe consequences, including:
Loss of Sensitive Data: Intercepted data can include login credentials, financial details, or personal communications, leading to identity theft or financial fraud.
Reputational Damage: For app developers and organizations, a data breach caused by eavesdropping can lead to loss of user trust and damage to the brand.
Regulatory Penalties: Failure to protect user data can result in violations of regulations like GDPR, HIPAA, or PCI DSS, leading to hefty fines.
Increased Cybercrime: Intercepted data can be sold on the dark web, fueling further criminal activities.
To mitigate the risks of eavesdropping, mobile app developers must adopt robust security measures. End-to-End Encryption (E2EE) stands out as one of the most effective solutions, ensuring that data remains encrypted from the sender to the receiver, rendering it useless to attackers even if intercepted.
What is End-to-End Encryption?
End-to-End Encryption (E2EE) is a powerful security mechanism designed to protect data during transmission. It ensures that only the sender and the intended recipient can access the content of a communication, effectively shielding it from any third parties, including service providers, hackers, and even governments.

How Does End-to-End Encryption Work?
At its core, E2EE leverages cryptographic techniques to protect data. Here’s a simplified explanation of how it operates:
1️⃣ Key Generation:
A pair of cryptographic keys is created: a public key and a private key.
The public key is shared with others, while the private key remains secure on the user’s device.
2️⃣ Data Encryption:
When the sender transmits data, it is encrypted using the recipient’s public key.
This process converts the plaintext message into ciphertext, making it unreadable.
3️⃣ Secure Transmission:
The encrypted data travels across the network to its destination.
Even if intercepted, the ciphertext remains unintelligible without the private key.
4️⃣ Data Decryption:
Upon receiving the encrypted data, the recipient’s private key decrypts it back into its original plaintext form.
This ensures that even if the data is intercepted during transmission, it cannot be deciphered without the correct decryption key.

E2EE vs Non-E2EE Real World Usecases
To help understand the importance of End-to-End Encryption (E2EE), let’s look at some real-world applications that either use E2EE for security or do not use it for efficiency and usability reasons.
✅ Apps that Use E2EE
▶️WhatsApp, Signal, iMessage
Messages are encrypted from sender to receiver, making them unreadable by service providers, hackers, or governments. However, this makes multi-device support more complex and causes delays in first-time setup due to key generation.
▶️Zoom (E2EE Mode)
Meetings are encrypted from sender to receiver, ensuring privacy.
Trade-off: Some features like cloud recording and live transcription, Live streaming, Zoom Whiteboard and some other features are disabled.
❌ Apps that Do Not Use E2EE
▶️Google Drive, Dropbox
Files are encrypted in transit and at rest, but not E2EE, meaning the provider can access them.
Reason: This allows file previews, search indexing, and AI-powered organization but sacrifices user privacy.
▶️Telegram (by default)
Regular chats are NOT E2EE (only “Secret Chats” are). Messages are stored on Telegram’s servers.
Reason: Allows seamless multi-device syncing and message retrieval, but at the cost of privacy.
▶️Zoom (default mode)
Video calls are encrypted in transit, but Zoom’s servers can decrypt them to process features.
Reason: Allows cloud recording, real-time transcription, and better performance.
Why Some Services Choose NOT to Use E2EE?
While E2EE provides maximum privacy, it limits functionality in some applications. Many companies choose not to implement E2EE due to:
Multi-Device Syncing Challenges → Without server-side access to messages, syncing across multiple devices becomes harder.
Search & AI Limitations → Encrypted files/emails/messages cannot be indexed for search or analyzed for AI recommendations.
Performance & Cost Considerations → Encrypted files are larger, increasing storage & processing costs for cloud services.
Key Features of End-to-End Encryption
Data Confidentiality: E2EE ensures that only the sender and recipient can access the communication, preventing unauthorized access.
Tamper Detection: Any attempt to modify encrypted data during transmission will corrupt the ciphertext, alerting the recipient to potential tampering.
No Intermediary Access: Even service providers facilitating the communication cannot access the content, ensuring privacy.
How End-to-End Encryption Works in Mobile Apps
End-to-End Encryption (E2EE) in mobile apps is a practical implementation of cryptographic principles to secure communication. Here’s a detailed breakdown of how it works in the context of mobile applications:
Key Components of E2EE
To implement E2EE effectively, mobile apps rely on the following components:
1️⃣ Public and Private Keys (Asymmetric Encryption):
Each user has a unique pair of keys:
A public key to encrypt messages, which is shared with others.
A private key to decrypt messages, which remains securely stored on the user’s device.
2️⃣Symmetric Keys for Efficient Data Encryption:
A temporary symmetric key (e.g., AES key) is used for encrypting bulk data efficiently.
This symmetric key is encrypted using the recipient’s public key and sent along with the data.
3️⃣Secure Storage:
Private keys are securely stored on the device, using mechanisms like:
Secure Enclave (iOS).
Android Keystore (Android).
4️⃣Network Security:
Communication channels are secured using Transport Layer Security (TLS) to prevent interception during data transmission.

Challenges in E2EE Implementation
1️⃣ Key Management:
Safely generating, distributing, and storing cryptographic keys is complex and critical for ensuring security.
2️⃣ Performance:
Asymmetric encryption, such as RSA, can be computationally expensive, leading to potential performance bottlenecks in real-time applications.
3️⃣ Key Revocation:
Managing scenarios where keys are compromised or need to be invalidated is a significant challenge in maintaining trust and security.
4️⃣ User Experience:
Balancing strong security measures with a seamless user experience can be difficult, especially when encryption introduces delays or additional steps.
Key Management: The Core of E2EE
One of the biggest challenges in End-to-End Encryption (E2EE) is key management. Since only the sender and receiver should have access to encrypted data, the system must handle key synchronization, updates, and revocation without exposing private keys. Poor key management can break the security of an otherwise well-encrypted system.
1️⃣ Key Synchronization:
Since encryption keys must remain private to users, E2EE systems use various strategies to synchronize and distribute keys securely:
▶️Public Key Exchange (For Secure Communication Between Users)
In E2EE messaging apps, users need a way to encrypt messages for each other without sharing private keys.
The solution is asymmetric encryption, where:
Each user has a public key (shared with others).
A private key (kept secret on their device) decrypts incoming messages.
How It Works:
When User A wants to send a message to User B, the server provides User B’s public key.
User A encrypts the message with that key.
The encrypted message is sent and only User B can decrypt it using their private key.
2️⃣ Key Updates:
Key updates ensure that even if a key is compromised, past and future messages remain protected. They are especially important in applications that handle sensitive communications, such as messaging apps, financial transactions, and secure storage services.
Encryption keys can become vulnerable over time due to:
Long-Term Key Exposure → The longer a key is in use, the higher the risk of compromise.
Device Theft or Hacking → If an attacker gains access to a device, they could steal private keys.
Advancements in Cryptanalysis → Encryption methods improve, and older keys may become weaker over time.
Insider Threats or Government Requests → Some services may be pressured to reveal encryption keys, but key updates limit exposure.
Types of Key Updates in E2EE:
▶️Session-Based Key Updates (Perfect Forward Secrecy)
Every conversation session or even every message gets a new encryption key.
Even if one key is compromised, past and future messages remain secure.
▶️Periodic Key Rotation
Encryption keys are updated every set period (e.g., every 90 days).
Old messages remain encrypted with the previous key, while new messages use the updated key.
▶️Manual Key Updates & User-Initiated Key Change
Users can manually generate and distribute new encryption keys when needed.
Recipients must re-verify the sender’s identity (e.g., exchanging new public keys via a trusted channel).
▶️Re-Encryption of Old Data with New Keys
When an encryption key is updated, old encrypted files/messages are re-encrypted with the new key.
This ensures that even if a previous key is leaked, past data remains secure.
2️⃣ Key Revocation:
Key revocation is a crucial part of End-to-End Encryption (E2EE) that ensures compromised, lost, or outdated encryption keys are no longer valid. Since E2EE is designed to keep data private between the sender and recipient, revoking keys must be handled in a way that maintains security while allowing users to regain control if their private keys are lost or compromised.
Unlike traditional encryption systems where a central authority (e.g., a server) can easily revoke access, E2EE does not allow servers to manage or store private keys. This makes key revocation a complex challenge, as the system must ensure that revoked keys are no longer used without compromising past communications.
Importance of Key Revocation:
Lost or Stolen Devices → If a user’s device is lost or stolen, the encryption keys stored on that device could be compromised.
Hacked or Leaked Keys → If a private key is exposed in a data breach, an attacker could decrypt intercepted messages.
User Identity Change → When users change their devices or accounts, old keys should be revoked to prevent unauthorized access.
Forward Security → Ensuring that past communications remain secure even if a key is revoked.
Without a proper key revocation mechanism, an attacker with a stolen key could continue decrypting new messages indefinitely.
Methods of Key Revocation in E2EE Systems:
▶️Manual Key Revocation by the User
Users generate a new encryption key and notify their contacts.
The old key is marked as revoked, so it is no longer used for encrypting new messages.
A verification process (e.g., scanning a QR code) may be required to confirm the key update.
▶️Automatic Key Revocation via Expiry
Encryption keys are automatically set to expire after a certain period.
When a key expires, the system generates a new key and updates all future communications.
Some systems use ephemeral session keys (one-time-use keys) to ensure automatic revocation.
▶️Certificate Revocation Lists (CRLs) & Revocation Servers
A revocation list is maintained, identifying invalidated keys.
Before encrypting a message, the system checks the revocation list to ensure the recipient’s key is still valid.
Public Key Infrastructure (PKI) is often used for certificate-based encryption, such as email encryption (S/MIME).
▶️Key Revocation Through Multi-Device Authentication
If a user’s device is lost, they can log in from another authenticated device and revoke access to the lost device.
Encryption keys are synced across trusted devices, and the revoked device can no longer decrypt messages.
How E2EE Affects Backend Capabilities
When data is encrypted end-to-end, even the service provider cannot access or analyse it. This creates significant challenges for applications that rely on data analytics, search indexing, AI models, and personalization.
❌ 1. Search & Indexing Becomes Impossible
Cloud-based services like Google Drive and Dropbox allow users to search their files because their data is not encrypted end-to-end.
In contrast, services like ProtonMail (which uses E2EE for emails) cannot provide full email search — only metadata (like subject lines) is searchable.
Trade-off: Encrypted data cannot be indexed, making efficient searches harder.
❌ 2. Loss of AI & Machine Learning Insights
Many services, including Google Photos, Gmail, and Apple Photos, use AI to categorize and suggest content (e.g., recognizing faces, recommending emails).
E2EE prevents this because AI models cannot analyse encrypted data and will not allow them to train them.
Example:
Google Photos can auto-tag and organize your pictures based on AI analysis.
If photos were E2EE encrypted, Google would not be able to process or tag them.
❌ 3. No Behaviour-Based Personalization
Platforms like Spotify, Netflix, and YouTube analyse user behaviour to recommend content.
E2EE prevents data-driven personalization since the platform cannot analyse user preferences directly.
Example:
Netflix recommends shows based on your watch history.
If Netflix were fully E2EE, the company couldn’t analyse viewing patterns — leading to less accurate recommendations.
❌ 4. Encrypted Data Cannot Be Used for Fraud Detection
Many platforms use backend machine learning models to detect fraud (e.g., banks analysing transaction patterns).
With E2EE, the backend cannot inspect transaction details, making fraud detection harder.
As a workaround for these limitations, some companies use alternative methods to balance security with usability by applying the followings:
✅ 1. Metadata-Based Analysis
While message content is encrypted, apps still analyze metadata (e.g., timestamps, IP addresses, device types).
Example: Telegram encrypts messages but logs metadata to improve delivery performance.
✅ 2. Client-Side AI & Search
Instead of analysing data on the backend, some apps process encrypted data on the user’s device.
Example: Apple’s Face ID & on-device Siri process data locally rather than in the cloud.
The Trade-off: Privacy vs. Functionality
🔐 E2EE ensures maximum privacy, but it limits many features users take for granted, like search, personalization, AI-driven recommendations, and fraud detection. 📊 If backend insights are critical, developers may need a hybrid encryption model where only the most sensitive data is E2EE, while other data remains accessible for analysis.
When do we need E2EE?
End-to-End Encryption (E2EE) is a cornerstone of secure communication in modern mobile applications. But when should you implement E2EE in your app? The answer lies in understanding the nature of the data being handled and the level of privacy users expect. Below are some common scenarios where E2EE is essential:

Communication Privacy: Apps like messaging platforms, VoIP services, and video conferencing tools require E2EE to ensure that private conversations remain confidential and accessible only to the intended participants.
File Sharing: When users share sensitive documents or media files, E2EE guarantees that the content is protected from interception or unauthorized access during transmission.
Collaborative Work: In enterprise apps or team collaboration tools, E2EE secures communication and shared data, safeguarding corporate information and intellectual property.
Cloud Storage: Applications that store sensitive data in the cloud can use E2EE to protect it from unauthorized access, even by the service provider hosting the data.
The diagram below illustrates these key scenarios where E2EE plays a vital role in ensuring data security and user trust. If your app handles any of these use cases, implementing E2EE is a must to meet user expectations and industry standards for privacy.
ECC vs. RSA for Asymmetric Encryption

Asymmetric encryption plays a crucial role in End-to-End Encryption (E2EE) by enabling secure key exchanges and authentication. Traditionally, RSA (Rivest-Shamir-Adleman) has been widely used for public-key encryption, but in recent years, Elliptic Curve Cryptography (ECC) has become the preferred choice due to its stronger security, better performance, and lower computational cost.
✅Smaller Key Size for the Same Security Level
One of the biggest advantages of ECC over RSA is that ECC provides the same level of security with much smaller key sizes.
✅ Better Performance (Faster Encryption & Decryption)
ECC is significantly faster than RSA in key generation, encryption, and decryption operations.
RSA encryption is fast, but decryption is slow (requires large integer multiplications).
ECC operations are much faster due to their smaller key sizes and lower computational overhead.
✅ Stronger Security Against Quantum Computing
One of the biggest threats to RSA encryption is quantum computing.
Shor’s Algorithm (a quantum algorithm) can efficiently break RSA by factoring large numbers.
ECC is also vulnerable to quantum attacks, but it requires far more quantum resources to break compared to RSA.
How to implement E2EE in Your Flutter App
Incorporating End-to-End Encryption (E2EE) into a Flutter app ensures that sensitive data is protected throughout its journey from sender to receiver. With E2EE, even if communication is intercepted, the data remains unreadable without the decryption keys. Implementing E2EE might sound complex, but with Flutter’s flexibility and packages, it becomes a streamlined process.
In this part, we’ll focus on a step-by-step guide to implementing E2EE in your Flutter app using My new Package, which contains some cryptography algorithms (more to be added..) and will have additional encryption functionalities in the near future. the package is:🔥DashCrypt🔥
We’ll cover key concepts like generating encryption keys, encrypting and decrypting messages. By the end, you’ll have a practical understanding of how to secure your app’s communication channels effectively.
What is Dash Crypt?
DashCrypt is a powerful and flexible encryption and decryption package for Flutter and Dart. It supports a wide range of modern and classical cryptographic algorithms, making it ideal for developers looking to integrate secure encryption into their projects. DashCrypt also provides utilities for secure key and IV generation, ensuring robust security. Designed for simplicity, performance, and scalability, DashCrypt is the perfect solution for all your encryption needs.
Currently it supports the following Encryption Algorithms:
AES with (CBC, CFB, ECB, GCM modes) & Key Sizes (128,192,256 bits)
Classical Ciphers (Affine, Caesar, Columnar Transposition, Monoalphabetic, Playfair, Rail Fence, Vigenere)
⏳Other modern Algo. & Encryptions ‘ll be added ⏳
Now Let’s Get our hands dirty in code 👨💻

Steps to use Dash Crypt:
1. Add the DashCrypt package to your pubspec.yaml:
2. Add imports to the top of the file where you want to use Talsec:
3. Start use the needed Algorithm for encryption/decryption like the following:
📌AES Algorithms
▶️Encryption
▶️Decryption:
📌Generating IV & Keys
▶️ Generate IV depending on the mode
▶️ Generate Key depending on the size
Now we used the package to encrypt/decrypt our data in several ways using modern algorithms and it’s now can be sent securely to the server.

Conclusion
In today’s digital landscape, where privacy is a growing concern, implementing End-to-End Encryption (E2EE) is more than just a technical feature — it’s a commitment to protecting your users’ data and fostering trust. By ensuring that information remains encrypted from sender to receiver, E2EE acts as a powerful shield against eavesdropping and data breaches, safeguarding sensitive communications even in the face of potential threats.
Throughout this guide, we’ve unpacked the essentials of E2EE, explored its benefits, and walked step-by-step through its implementation using the DashCrypt package in Flutter. From generating secure keys to encrypting and decrypting messages, you now have the tools to integrate robust encryption into your app with confidence.
By prioritizing E2EE, you’re not only addressing user privacy but also enhancing your app’s security posture, and positioning your app as a trusted solution in a competitive market. The effort you put into securing your app’s communication channels today will pay off by providing users with peace of mind and safeguarding your reputation as a developer.
Take the next step: refine your implementation, explore advanced use cases, and stay informed about evolving encryption standards. Security is a journey, not a destination — one where your dedication will make all the difference.

Your Journey Through This Guide Ends Here — But the Conversation Doesn’t Have To! 🙋♂️
Thank you for sticking with me through this guide on implementing End-to-End Encryption (E2EE) in Flutter apps! 🎉 I hope the steps, insights, and tips shared here have empowered you to build more secure and privacy-focused applications.
If you have any questions, suggestions, or want to dive deeper into any part of the article, I’d love to hear from you! Feel free to comment or suggest anything, Let’s continue the conversation and work together to make mobile apps safer for everyone. 💬😊

Last updated
Was this helpful?

