ApkSignatureKiller: How It Works and How Talsec Protects Your Apps
In this article, we will explore how Android protects against app tampering, discussing not only how ApkSignatureKiller works, but also the mechanisms behind.
Introduction
Ever wondered how your Android phone can tell if that Instagram app you're about to install is the genuine application, or just a sneaky clone repackaged by a hacker with malicious intent? That's where APK signatures come in – they're the digital gatekeepers of the Android app world! Think of them as a high-tech, unforgeable seal of authenticity stamped on every app, verifying its true origin and guaranteeing the code hasn't been illicitly altered since the developer signed off on it. This critical verification happens every time you install or update an app, acting as an invisible shield that ensures the software you're running is legitimate and safe.

How does the Android signature verification work?
Android apk sign verification has mainly two steps:
1. Signing
When development is complete, the developer signs the app using a private key. This process generates a digital signature of the app's contents and embeds the developer's public key certificate within the APK file.
2. Verification
This process is performed by the Android OS on the device before the installation of an app.
First, the Android package manager calculates a
cryptographic hashof the APK's contents.Next, it extracts the developer's public key certificate from the APK and uses it to decrypt the digital signature. This decryption reveals the
original hashof the app as calculated by the developer.Finally, the
hash calculated on the device is compared to the developer's original hash. If they match, it confirms that the APK's contents have not been tampered with since it was signed.

To prevent anyone from bypassing this verification mechanism, Android utilizes several signature schemes. The primary difference between them is how they sign the application and store the resulting data inside the APK:
v1 (JAR Signing): This original scheme individually signed each file within the APK and stored the signature data inside the
META-INF/directory (e.g.,MANIFEST.MF`, `CERT.SF). This method was computationally slow and had a critical flaw: it did not verify the entire APK file. Sections like the ZIP metadata were left unsigned, creating an attack vector where malicious code could be injected into the APK without invalidating the signature.v2 Scheme: Introduced in Android 7.0, this scheme verifies the entire APK file as a single blob. The signature is stored in a dedicated
APK Signing Block, located just before the ZIP Central Directory. This approach is significantly faster and closes the vulnerabilities present in the v1 scheme. However, this scheme did not originally support signing key rotation, meaning a developer could not change their signing key without breaking updates for their app.v3 Scheme: Introduced in Android 9.0, this scheme is very similar to v2 but adds support for
signing key rotation. It includes an attribute in theAPK Signing Blockthat holds a history of signing certificates. This allows developers to change their app's signing key while enabling the app to be verified using either the new or older keys, ensuring seamless updates.v4 Scheme: This scheme was introduced to support streaming installs, allowing for parts of an app to be used before the entire APK is downloaded. For v4 signing, a
Merkle hash tree of the APK's contentsis calculated, and its root hash is stored in a separate file named.apk.idsig. This allows for the incremental verification of individual blocks of the file as they are streamed to the device.
Vulnerabilities related to Android Signatures
The methods employed by ApkSignatureKiller are the modern versions of critical vulnerabilities of Android signature verification process.
1. The famous Master-Key vulnerability: This critical vulnerability exploited a discrepancy in how Android handled ZIP archives . An attacker could include two files with the same name within an APK. The package installer would process one file when verifying the signature, while the Dalvik/ART runtime would execute the other, malicious file. This allowed an attacker to inject and execute arbitrary code within a validly signed application, effectively bypassing the v1 signature check.
2. The Janus vulnerability: This vulnerability specifically targeted the v1 signature scheme. An attacker could prepend a malicious DEX file to the beginning of a legitimate, signed APK file. Because the v1 signature verifier would check the integrity of the ZIP entries but ignore the header of the file, it would still validate the application as authentic. However, the Android runtime would see the malicious DEX file at the start and execute its code, effectively running a malicious payload while the app appeared legitimate. This is simlar to the methods used to bypass v1 signature scheme by the apkSignatureKiller application .
The ApkSignatureKiller
The infamous ApkSignatureKiller application actively bypasses Android's entire signature verification system. This capability is frequently exploited to tamper with critical applications, such as banking apps, which are then used on a device, creating a major security headache for developers who rely on signature checks to ensure app integrity.
Let us take an example of an Android app signed by v1 signature scheme named victimApp2 :

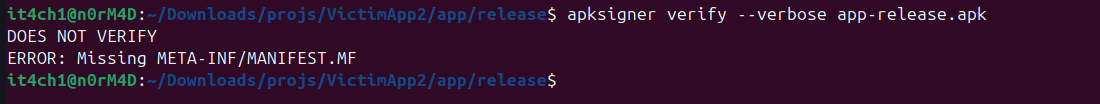
We can also check which signature schemes are verified inside a fully built apk using apksigner tool. This shows that the apk has been signed using the v1 signature scheme.
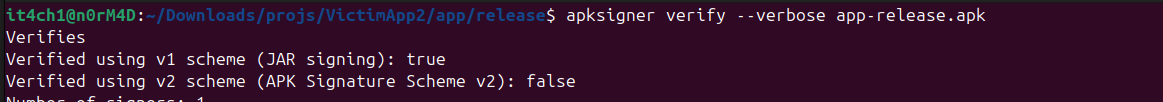
Now let's try to install the apk inside the Android emulator with < Android 7.0 to ensure that we are able to install apk with just v1 signature scheme. With v1 scheme enabled we are easily allowed to install the apk on the device.
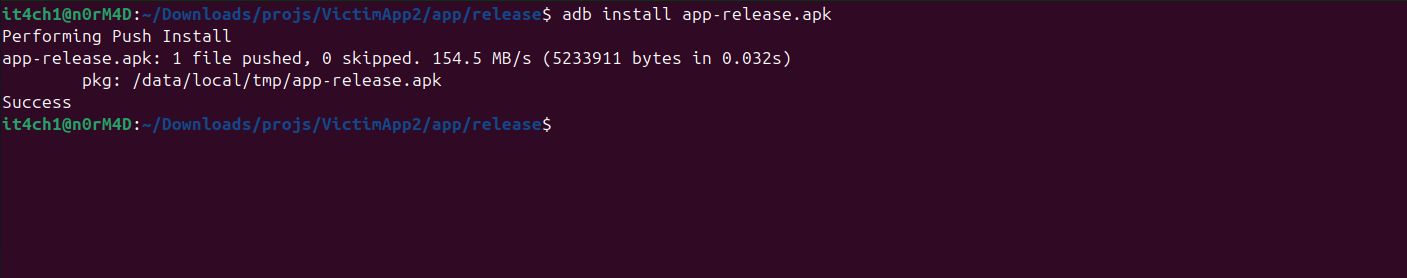
Now let's try the same with the unsigned apk on the same device. This tells us that the apk is unsigned and cannot be verified. The device also denies to download the unsigned application.
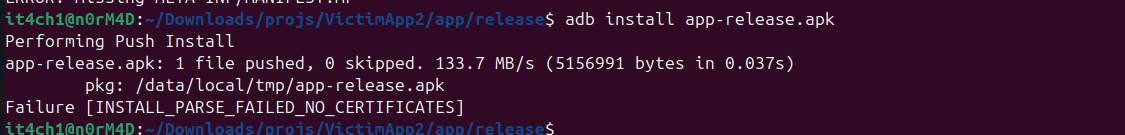
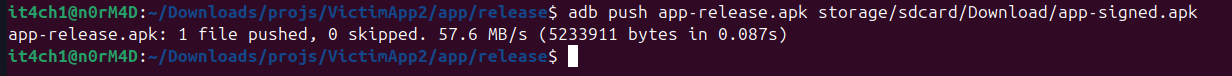
Here enters the ApkSignatureKiller who changes everything. Now let's just hook and modify our signed installed application using the ApkSignatureKiller. For this we have to push our signed application into the directory that can be accessed by the ApkSignatureKiller app just like the external storage directory.
Let's open our evil app
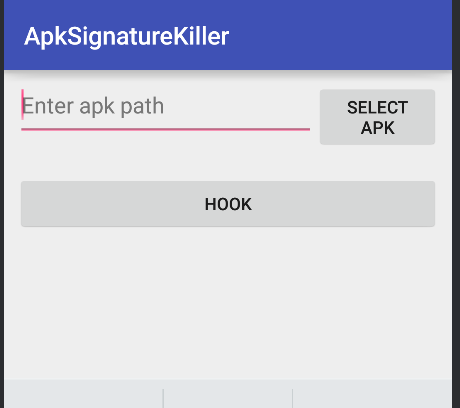
Now just choose the signed app from the external directory and then press the
Hookbutton.
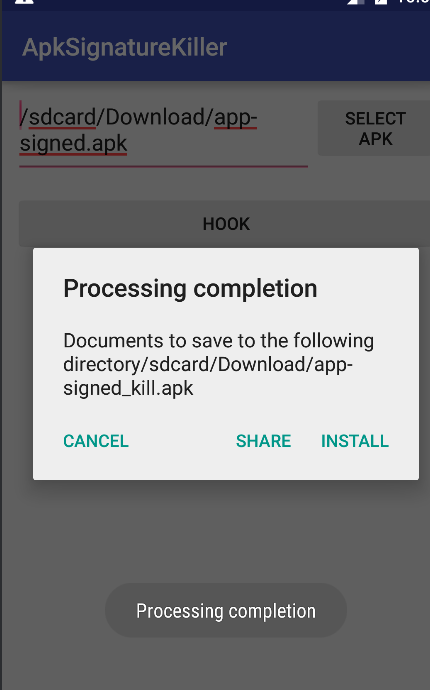
Press
Installand guess what we are able to install the app with the killed signature verification mechanism.
We can also verify if our new app has been actually modified or not.
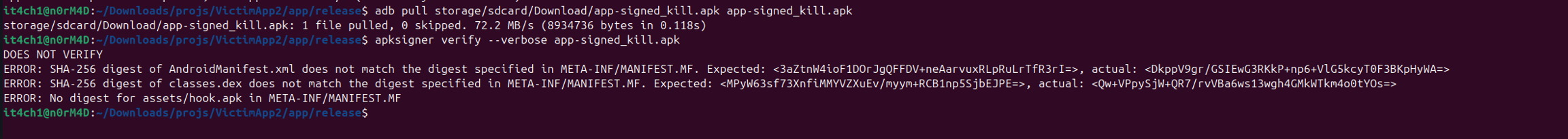
This shows that an unsigned, tampered application can be installed on a device without being detected by Android's security mechanisms. It proves that by using this method, it's possible to alter an app, recompile it, and install it without a valid signature, leaving the app's contents completely vulnerable.
To keep this article straightforward and easy to understand, I have used a simple demo application and focused on bypassing only the v1 signature scheme. However, it is crucial to understand that modern versions of ApkSignatureKiller and similar tools, are capable of bypassing the much more secure signature schemes. This makes them some of the most dangerous tools in the hands of attackers today.
Working of ApkSignatureKiller
But some of you with inquisitive minds might wonder: How does this tool actually work? How is it able to bypass the signature verification on an Android device ? 🙁
To bypass the signature check, the tool doesn't just remove the signature; it employs a more deceptive technique. It injects its own malicious code into the target application by hooking the specific part of the Android framework responsible for verifying an app's integrity. This injected code then intercepts the verification process and falsely reports to the system that the APK is still securely signed, even though its original signature has been stripped and its contents have been altered.
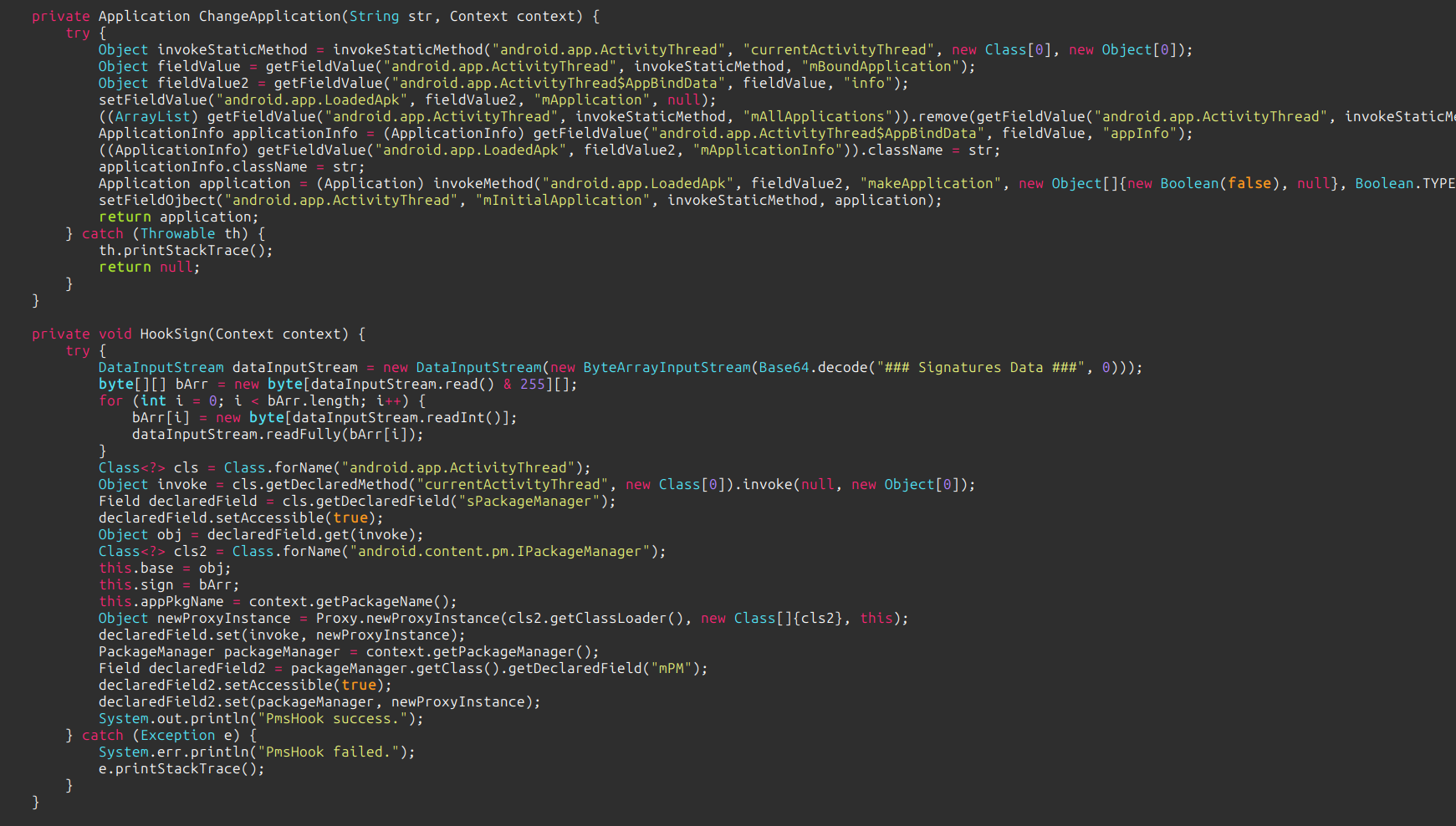
These are the methods used by it to hook the application and remove its signature file.
It basically hooks the classes like
PackageManagerorContextImplthat are generally used during reflection that helps in signature verification of the Android application.
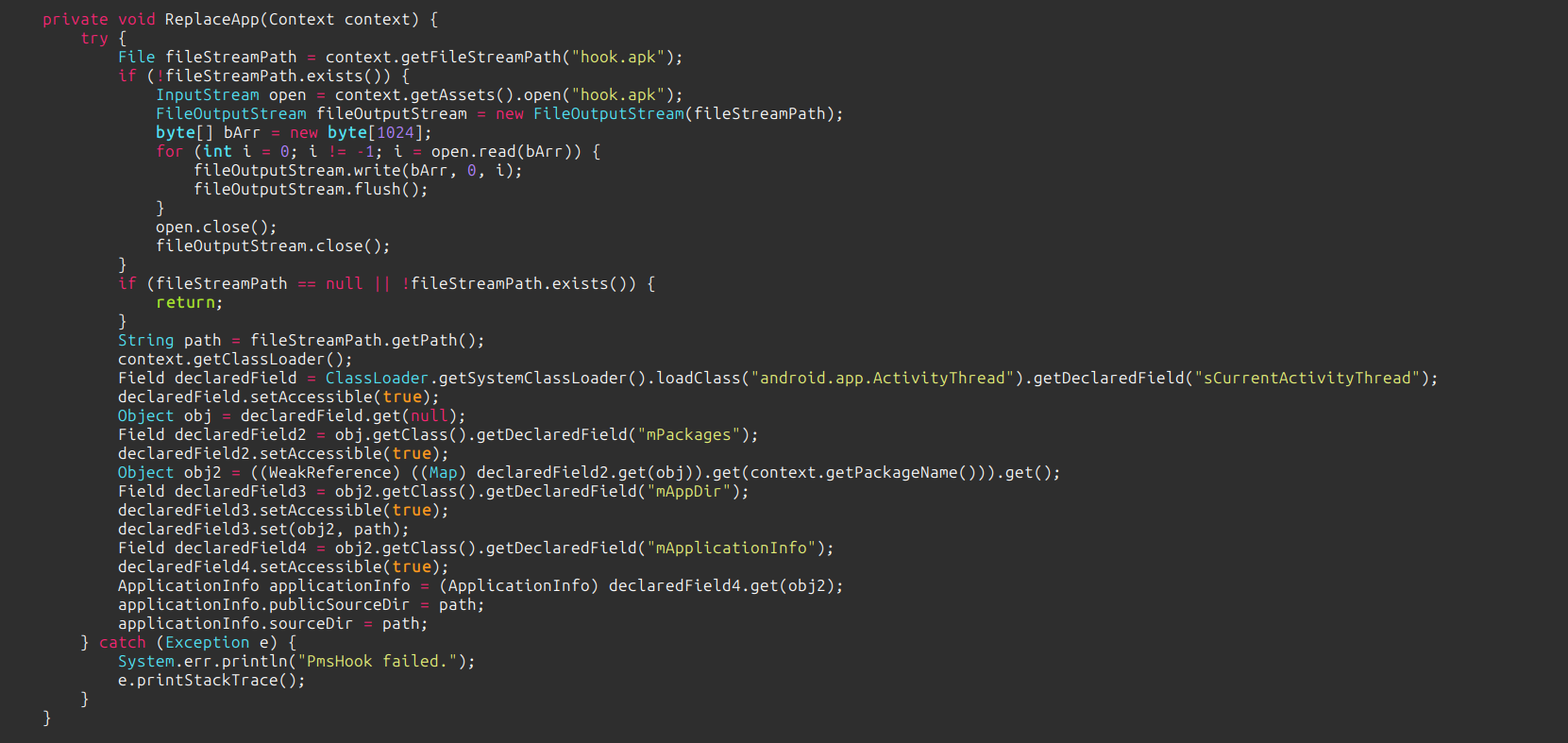
Then it uses this above method to replace the application with new application that does not have any signature verification mechanism and will always be verified by the Android signature verifier no matter how much the apk is tampered.
It hooks the code that fetches the signature file for verification and instead modifies the method to return true or verified always.
Why is it so crucial ?
Think of your Android device as a car and its signature verification system as a sophisticated car alarm. As long as the alarm is active, a thief cannot steal the stereo without setting it off.
However, a tool like ApkSignatureKiller acts as a master key that doesn't just break the window but cleverly disables the entire alarm system. Once the alarm is off, the thief can freely open the doors, steal the stereo, or even swap out the engine parts without anyone knowing.
This is precisely why signature verification is so crucial for an Android app. Without it, anyone could tamper with an app's contents, recompile it, and distribute their own modified version . Imagine the consequences: someone could unlock Spotify Premium for free, use cheats in a game like Clash of Clans, or, far more dangerously, bypass security measures in banking applications to authorize fraudulent transactions.
ApkSignatureKiller threatens the very foundation of Android's application security model. Despite continuous efforts to harden the platform, this tool often succeeds in its malicious goals.
But luckily, as developers, we are not helpless. There are concrete steps we can take to safeguard our applications against such attacks:
How to prevent tampering attacks with Talsec RASP+? [2 Months Free Trial!]

Talsec's RASP+ (Runtime App Self-Protection) offers a multi-layered defense to shield mobile apps from tampering and malicious tools like ApkSignatureKiller. These tools are built to bypass Android's fundamental security measure: verifying an app's digital signature. By disabling this check, an attacker can modify a legitimate app, inject malicious code, and then repackage it.
RASP protects against that with:
Signature and Certificate Verification: Unlike system-level checks that can be intercepted or disabled, RASP operates within the application itself. It continuously validates the app’s signature and signing certificate hash, making tampering significantly more difficult.
Code and Resource Integrity Checks: RASP doesn’t stop at verifying signatures—it actively monitors the application’s code and resources. If the app has been decompiled, modified, or augmented with malicious code, RASP flags and responds to these unauthorized changes.
Real-time Threat Response: When RASP detects a threat, it triggers a callback function—giving developers full control over how their app responds. Once integrated, you can implement callbacks such as
onRootDetected,onDebuggerDetected,onEmulatorDetected, and more. These powerful tools let you tailor defensive actions: show custom alerts, limit app functionality, or shut down the app entirely if the environment is compromised.
The onTamperDetected callback plays a crucial role in identifying and responding to signature verification issues within the application. This powerful layer of security is easy to integrate—any developer can add it in just minutes. With Runtime Application Self-Protection (RASP), strengthening your app's defenses has never been simpler.
Try it for free for 2 months and experience how effortlessly you can boost your app’s protection; check out https://talsec.app to request the trial.
written by Akshit Singh
Last updated
Was this helpful?

